In today’s digital age, pharmacies are not only entrusted with dispensing medications but also safeguarding sensitive patient information. With the rise of cyber threats, one of the most common and insidious methods used by hackers is phishing emails. These deceptive messages are crafted to trick recipients into revealing confidential information, compromising security systems, or even transferring funds unwittingly.
Phishing emails are the leading cause of healthcare data breaches.
Pharmacy owners and team members who handle a plethora of sensitive data daily, must be equipped with the knowledge to identify and thwart such malicious attempts. In today’s blog, we are going to explore ways to identify a phishing email so you know what to look for to avoid putting you business – and your patients – at risk.
How to Identify a Phishing Email
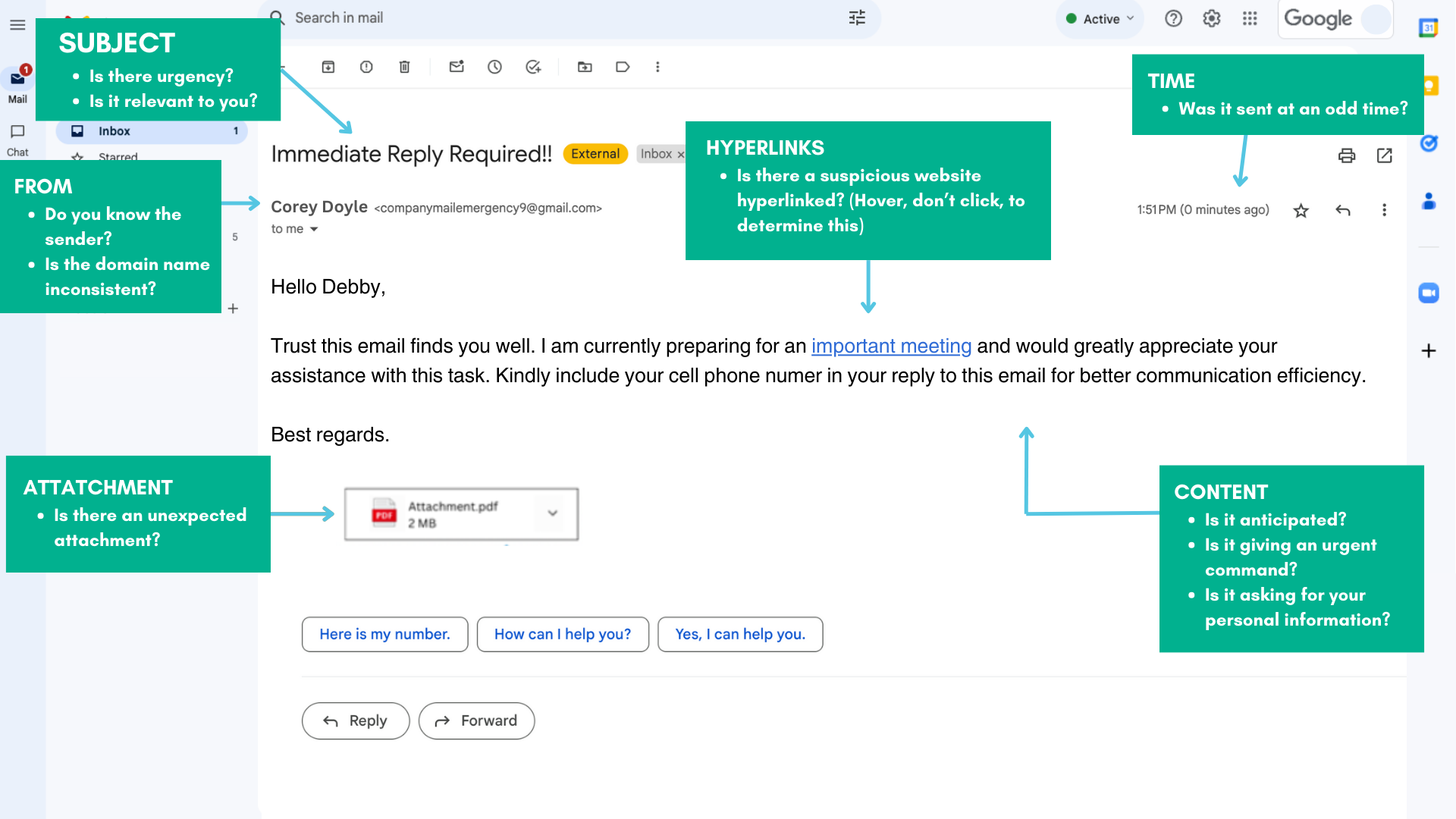
1) Verify the Sender
Phishing emails often mimic legitimate senders, but upon closer inspection, you may notice small discrepancies so be sure to check the sender’s email address carefully. Hackers frequently use slight variations or misspelled domains to deceive recipients. Legitimate emails from reputable sources will have consistent, correctly spelled addresses.
2) Evaluate the Content
Phishing emails commonly employ urgency or fear tactics to prompt immediate action. Be wary of messages that demand urgent responses or threaten dire consequences for inaction. Look out for grammatical errors, awkward phrasing, or generic greetings, as these are telltale signs of phishing attempts.
3) Inspect the Links
One of the primary methods phishers use to lure victims is by embedding malicious links within emails. Before clicking on any links, hover your cursor over them to reveal the actual destination. If the URL looks suspicious or doesn’t match the purported sender, refrain from clicking. Instead, manually type the URL into your browser for safe navigation.
4) Be Cautious of Attachments
While attachments may appear innocuous, they can harbor malware or ransomware designed to infiltrate your system. Only open attachments from trusted sources, and even then, scan them with reliable antivirus software before accessing. If you receive unexpected attachments from unfamiliar senders, err on the side of caution and refrain from opening them altogether.
5) Beware of Requests for Personal Information
Phishing emails often masquerade as legitimate institutions, such as banks or government agencies, or in some cases as an internal team member or manager that is requesting sensitive personal or financial information. Remember that reputable organizations will never ask for confidential details via email. If you’re unsure about the authenticity of a request, contact the organization or person directly through verified channels to confirm the legitimacy of the request.
Preventing Phishing Email Attacks
Even if you are familiar with all the phishing red flags, attacks are still possible and further measures should be taken to reduce these threats to the security of pharmacy operations and patient information. Below are some proactive measures to mitigate phishing attacks:
1) Delete & Report Suspicious Emails
Pharmacy staff should promptly delete (and do NOT forward) any emails that raise suspicion or appear to be phishing attempts. Report such emails to the pharmacy’s designated IT contact or email provider to investigate and potentially block similar phishing attempts in the future.
2) Educate Pharmacy Team Members
88% of healthcare workers have opened a phishing email.
Make sure that every team member who has access to your pharmacy networks is aware of the risks and signs of a phishing attack and knows the proper procedure for reporting suspicious emails. Hold a training session, and send out reminders (you might even want to share this blog post) to make sure everyone is on high alert for these scams.
3) Install a Firewall
Installing a well-managed pharmacy firewall solution is crucial for safeguarding the pharmacy’s network infrastructure against cyber threats – including phishing attempts. A properly configured firewall can block unauthorized access and filter out malicious email traffic, enhancing your cybersecurity and keeping patients’ sensitive information protected.


